Securing your devices using DNSSecuring your devices using DNS
We have long wondered why some of the more harmful webpages are not blocked more easily using DNS, and we finally found a system that does it for us.
We have long wondered why some of the more harmful webpages are not blocked more easily using DNS, and we finally found a system that does it for us.
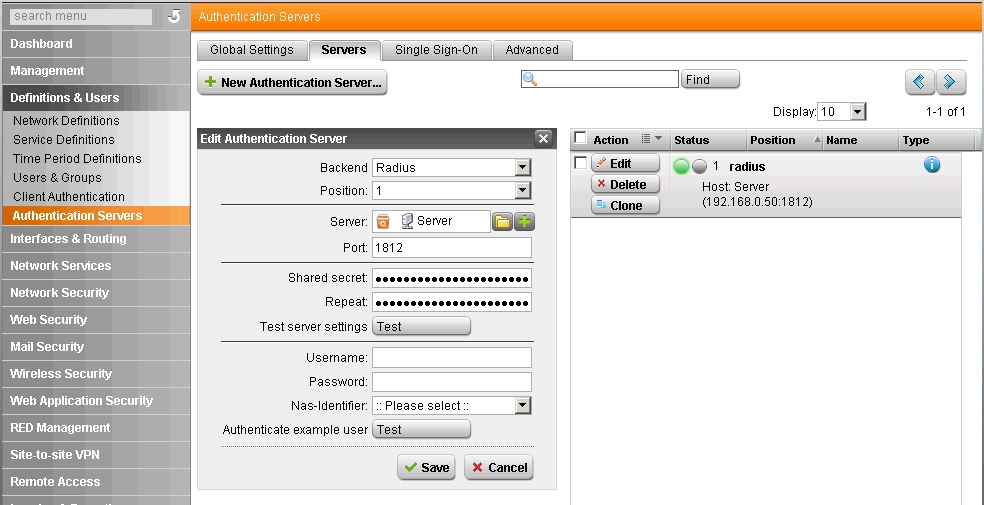
How to setup ASTARO (now sophos) UTM to authenticate with windows server 2003 through RADIUS. Step-by-step guide to getting it running. Step 1 – Add a usergroup to Authenticate against
Ethernet RJ45 Socket 10baseT Colour Code T568BPin No Description Colour1_____TX +_______Orange/White2_____TX -_______Orange3_____RX +_______Green/White4________________Blue5________________Blue/White6_____RX -_______Green7________________Brown/White8________________Brown_________________________________ RJ45 Cross Over Cable 10baseTRJ45 Male RJ45 Male1__________32__________63__________16__________2______________________________________ RJ45 100base-T4 Crossover male to maleName______Pin__Pin__NameTX_D1+____1____3____RX_D2+TX_D1-____2____6____RX_D2-RX_D2+____3____1____TX_D1+RX_D2-____6____2____TX_D1-BI_D3+____4____7____BI_D4+BI_D3-____5____8____BI_D4-BI_D4+____7____4____BI_D3+BI_D4-____8____5____BI_D3 It’s important