Install handbrake on CentOS8Install handbrake on CentOS8
Handbrake is easy to install and update on many linux distro’s because it is available as a package and can be installed without having to compile from source, simply for
Handbrake is easy to install and update on many linux distro’s because it is available as a package and can be installed without having to compile from source, simply for
We have long wondered why some of the more harmful webpages are not blocked more easily using DNS, and we finally found a system that does it for us.
To remove the apps that come pre-installed with windows 10, open a powershell window as Administrator, and paste the following
If your sick of paying for synchronization software that is overpriced or your running out of space using a free account, Syncthing is one answer, particularly if you have computers
If you need to access files on a remote computer (such as a webserver), you can use several different software to do this.
Microsoft Windows 10 home is easily modified to add the Remote Desktop features. These feature are only normally available in the Professional version of win10 (pro). You don’t need to
PowerShell takes the functionality of batch scripts to the next level and allows you to Remotely Lock & Shutdown computers using PowerShell. The following needs to be run on each
We recently had need to restart an app server exe automatically when the demonstration license it was running on caused the server to close regularly, annoying everyone trying to learn
Those of you that still use batch scripts (and why not … they are backwards compatible to older systems), will occasionally need to pause a script...
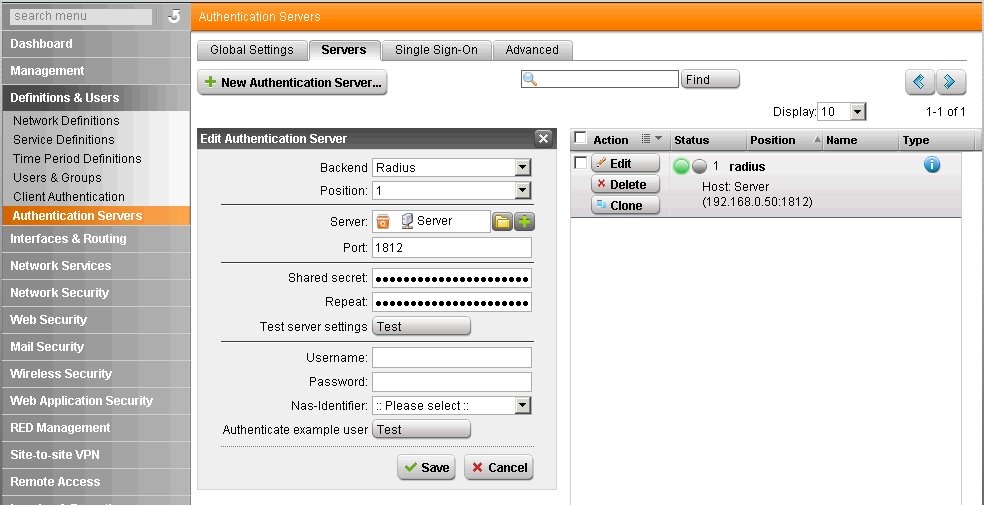
How to setup ASTARO (now sophos) UTM to authenticate with windows server 2003 through RADIUS. Step-by-step guide to getting it running. Step 1 – Add a usergroup to Authenticate against